Identifying a rival company stealing from you
I’ve spent a lot of my time doing security bits ‘n bobs for a large takeaway EPOS company. Usually this entails a full review all every repository to patch SQL injection vulnerabilities, Cross-Site Scripting vulnerabilities, and loopy logic vulnerabilities or mitigating random DDoS attacks, however on occasion I get to handle something a little different.
A lot of the images here have had details removed to protect the privacy of both those I work for and those I don’t.
I was monitoring the CPU Utilisation on AWS and noticed a weird spike to just over 10% utilisation (for some context, this is out of hours for most takeaways and CPU utilisation had been around 2% for the past few hours). Considering this database instance isn’t exactly underpowered I thought I’d take a look at it.
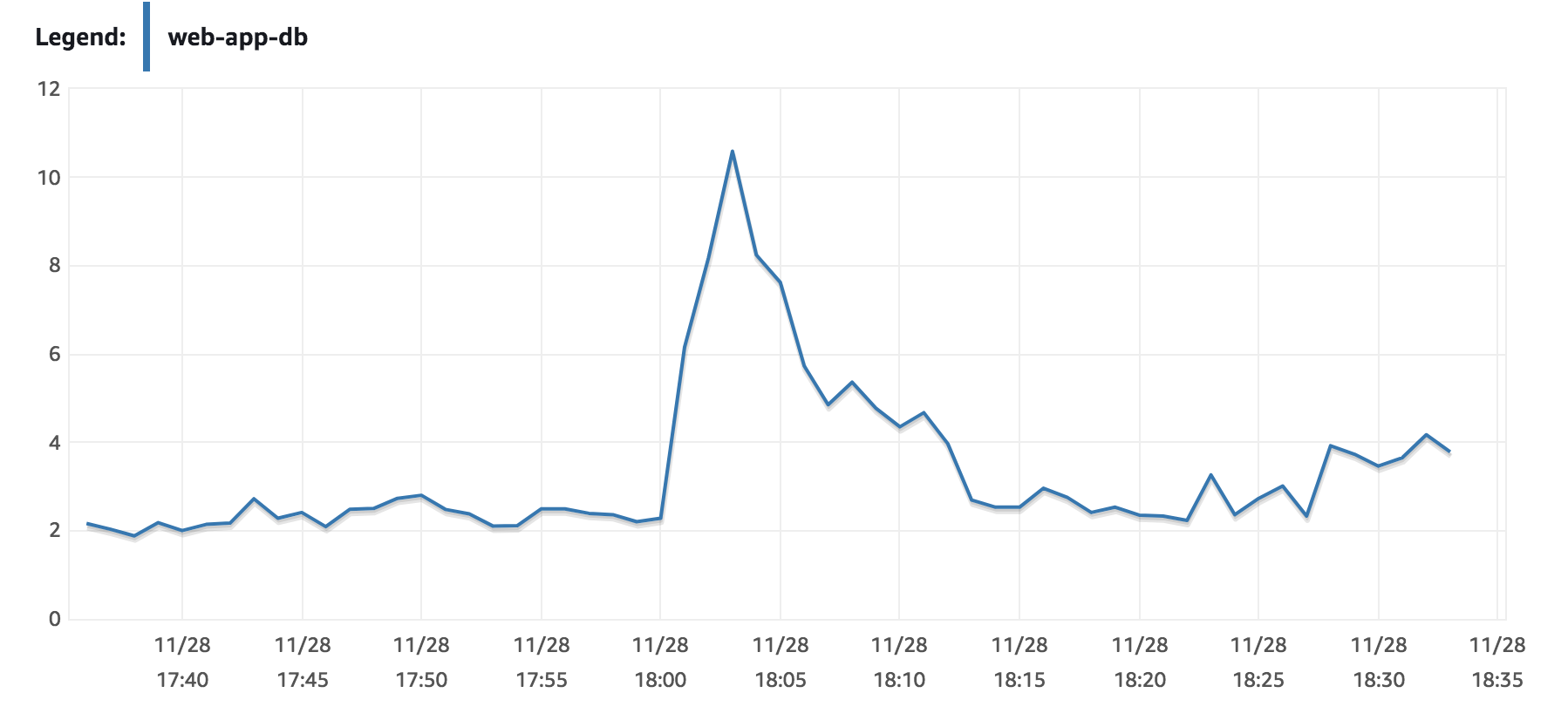
Monyog showed a pretty dramatic jump from 152k queries to 1.4m queries. There are a number of pages I’m aware of do a lot of heavy queries but for such a high change seems weird for normal traffic.
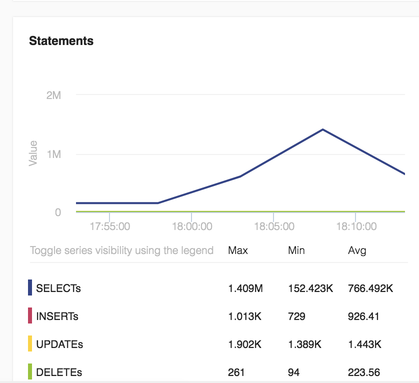
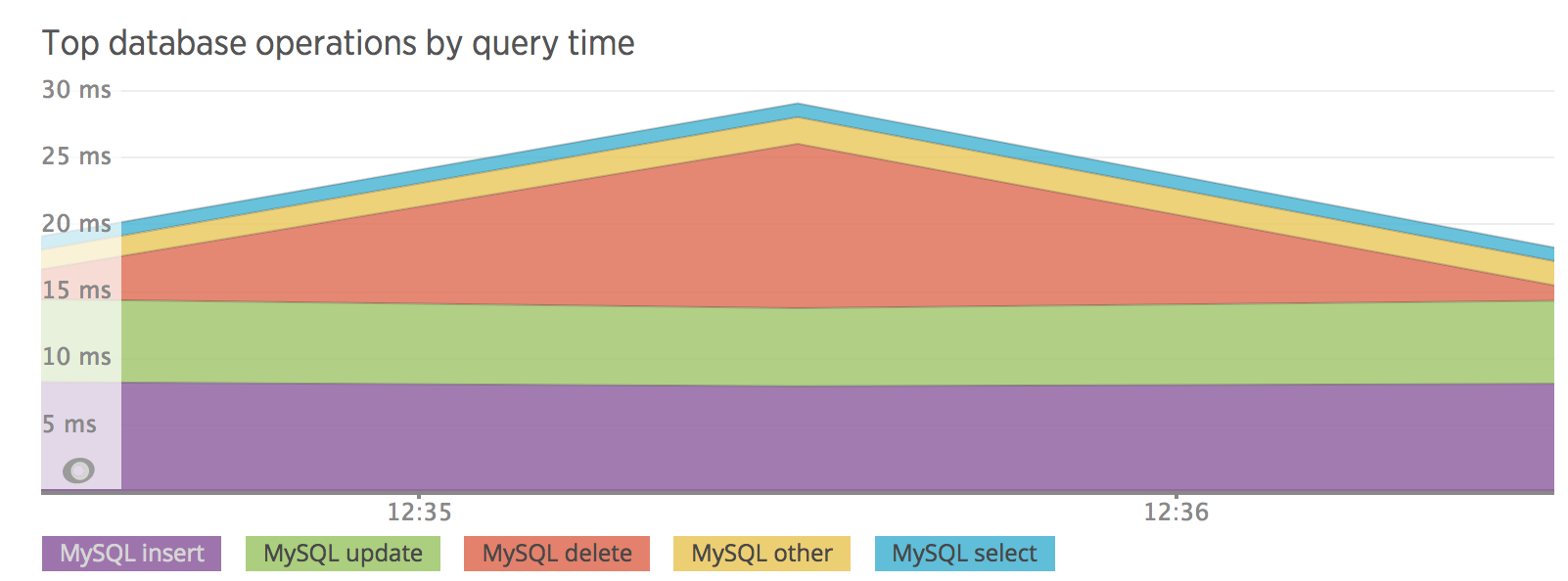
New Relic confirmed that a large amount of this time was dedicated to handling a few specific queries (DELETE, in this case) likely triggered from someone going on a few random pages.
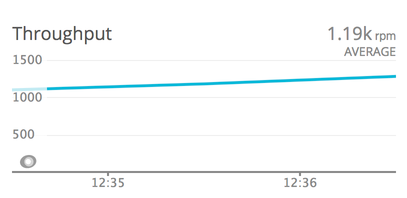
New Relic also allowed me to confirm that this wasn’t a DoS attack (or even an extremely weak DDoS attack) by verifying that the requests per minute hadn’t gone up dramatically.
I decided to look a little further into the matter so I took the opportunity to fire up my log analysis tool. I first decided to look at if there were any unusual numbers of requests from any IPs within the 10 minutes that might indicate a web crawler or a non-user pattern.
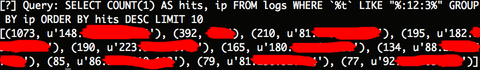
It was clear that there was one IP that stood out in this 10 minute period between 12:30 and 12:40. It had made 1073 requests on one of the web server instances (Normal users make between 20 to 100 requests. This was the only IP to make more than that during this timeframe). It was likely that there were another 1000 or so requests on the other instance that was also up.
While still on this server I decided to have a quick look at what the user agents for this IP were. A sign of a malicious web crawler is randomly selected user agents that change in quick succession. However this IP only had two User agents:
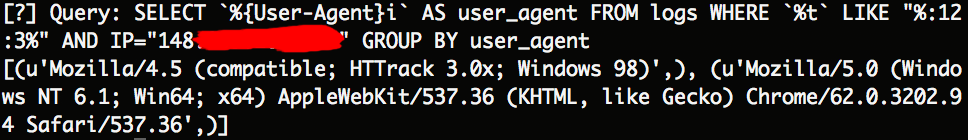
The one that caught my eye: Mozilla/4.5 (compatible; HTTrack 3.0x; Windows 98)
HTTrack, as many of you will know, is a popular website copier. As an EPOS company, there have been a number of times in the past where a rival company stealing a takeaway’s website and adapting it for them to use for their own product (One even forgot to change part of the ToS where the company name was formatted slightly differently).
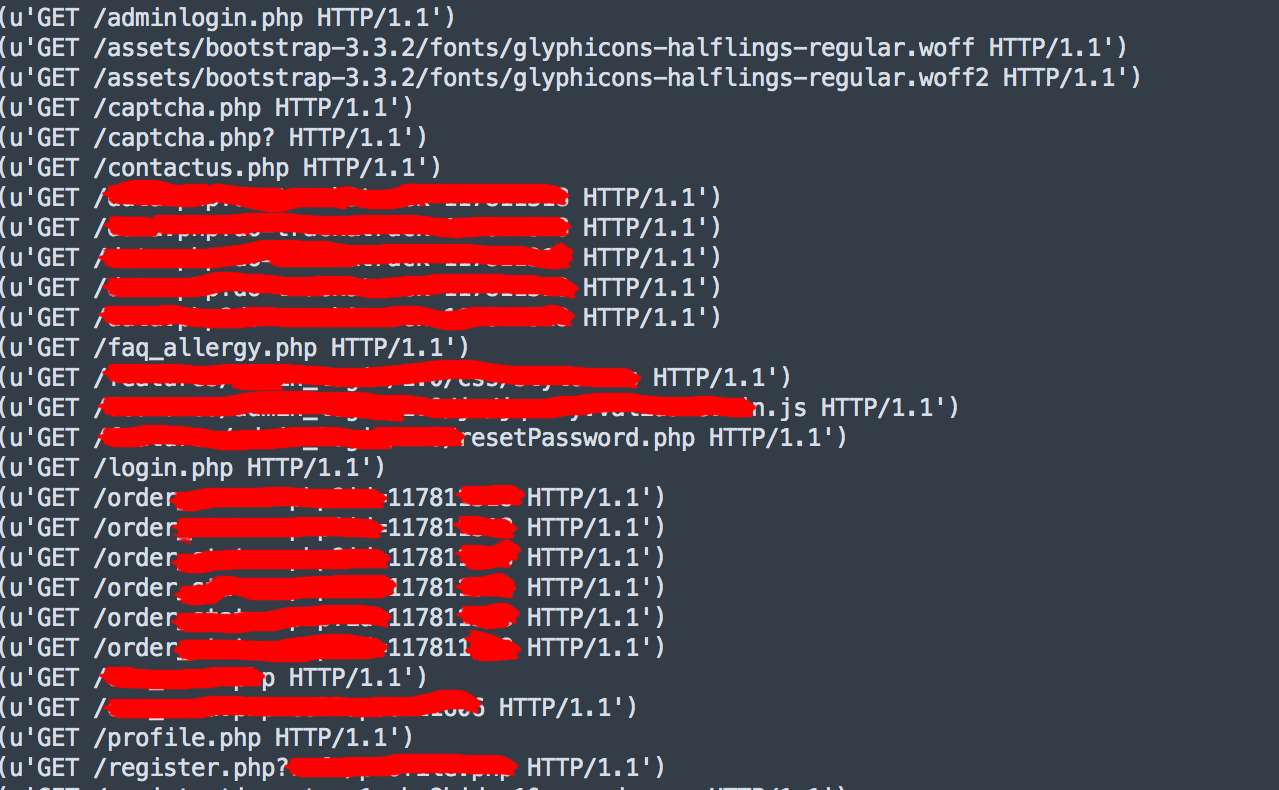
As I started to get a little more suspicious, I looked back over some of the files that were accessed and /order********.php?*****=11781***** jumped out at me. That wasn’t HTTrack, that was the person themselves who’d ordered food before running HTTrack.
I ran a query on the RDS to find out details of the order.

One thing I noticed was that the IP was different to the one I’d found in the log file. Almost as if the person had ordered food, jumped on a VPN, and ran HTTrack but forgot to close the order page that may have been sending AJAX requests to refresh the information displayed (Whoops!).
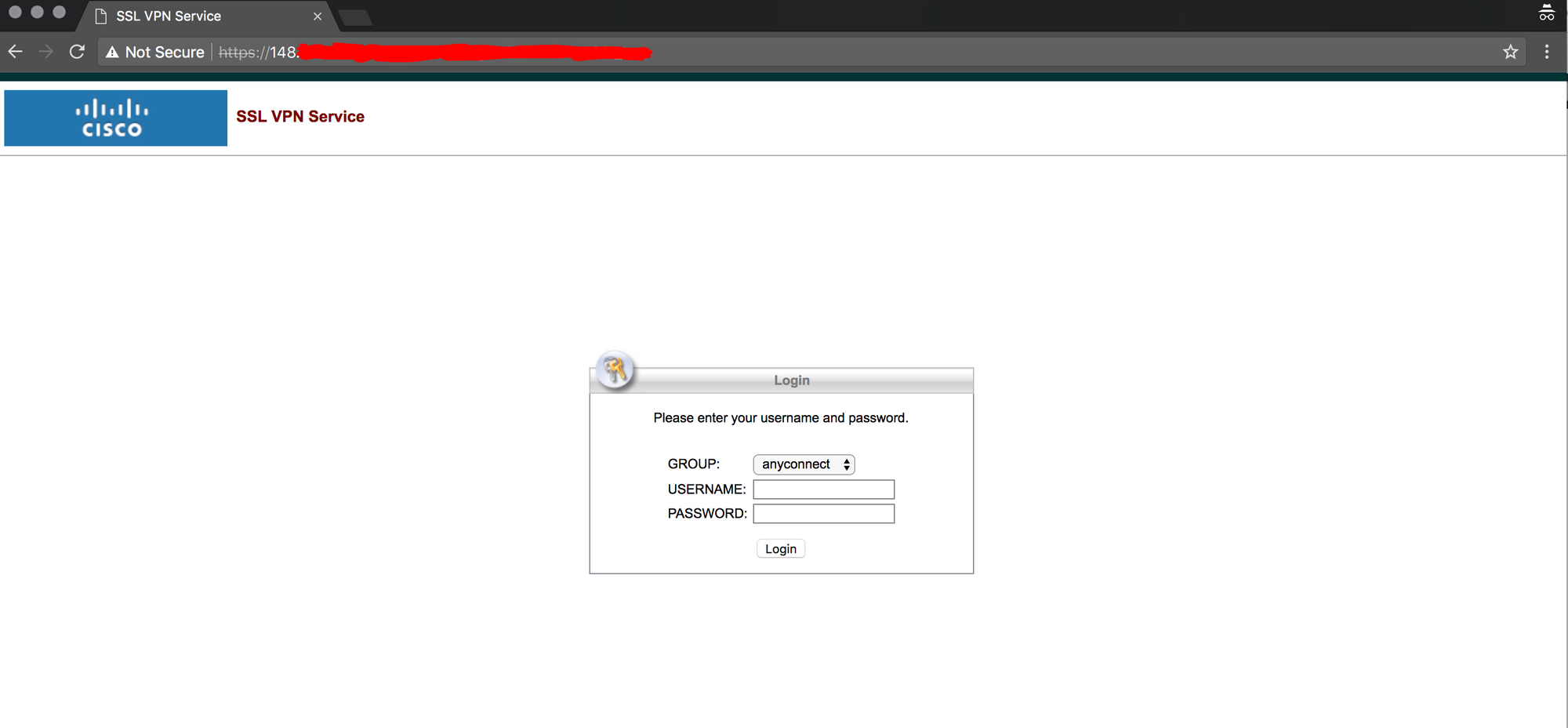
To confirm the VPN theory, I did a simple geolocate of both the order IP and the suspected VPN IP. The order IP was in a nearby city to the takeaway location whereas the suspected VPN was located a significant distance away from the takeaway. The suspected VPN IP linked to a Cisco VPN and so I felt a little more certain about my theory on the above events.
I did a quick query to see if either IP had been used before and I noticed something weird; A random EPOS name had been used on a few orders in either the comments section, or as the name… almost like an advert…
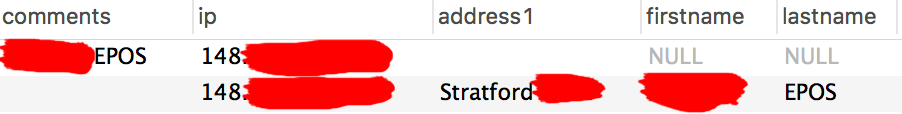
A quick search lead me to their website. Almost all the takeaways they handled were in the same city that the takeaway they were ordering from was located.
Finally I decided to do one more check to verify what I’d found even more. I whois’d their domain name.
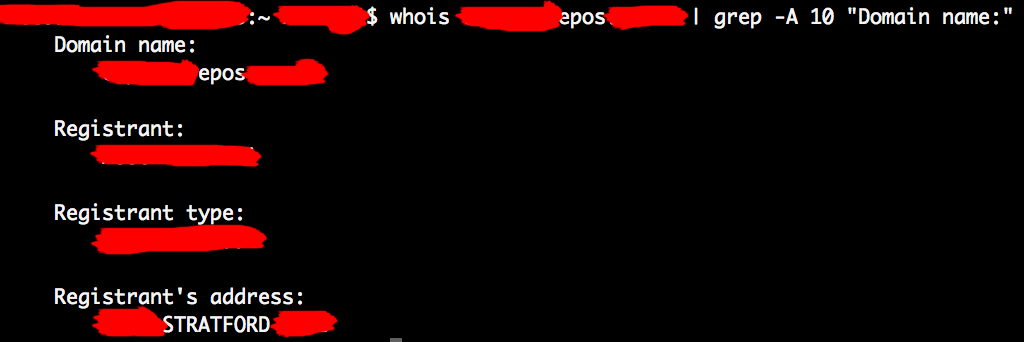
Surprise surprise, the domain was registered to the same street the orders were going to.
And with that, I passed what I’d found onto my manager and then the CEO.
Another day another job, eh?